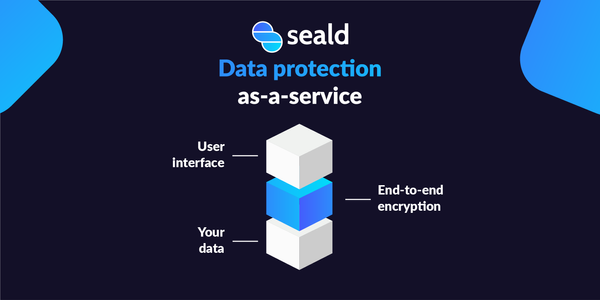
Let's decrypt together the 8 advantages of end-to-end encryption and discover why this technology has become a game changer for applications that collect sensitive data. But before diving into the 8 benefits that end-to-end encryption offers, it's essential to understand the problem this technology can address 🧐. Take the example of a "traditional" messaging application not encrypted end-to-end: During the transmission of a message, the sender sends their message to the application's server,







![[Interview] Introduction to cybersecurity](/_nuxt/image/680243.jpeg)